Most Read Articles
Most read articles are listed by the number of read for the previous three months.
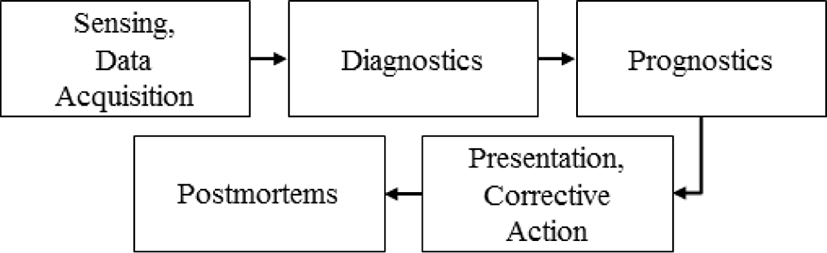
Optimal Weapons System Maintenance Using Prognostics and the Interface between an S1000D-based Interactive Electronic Technical Publication and Condition-based Maintenance
J. Def. Acquis. Technol. 2019;1(2):17-23.
https://doi.org/10.33530/jdaat.2019.1.2.17
HTML
PDF
PubReader
Last 3 months views: 1365
https://doi.org/10.33530/jdaat.2019.1.2.17
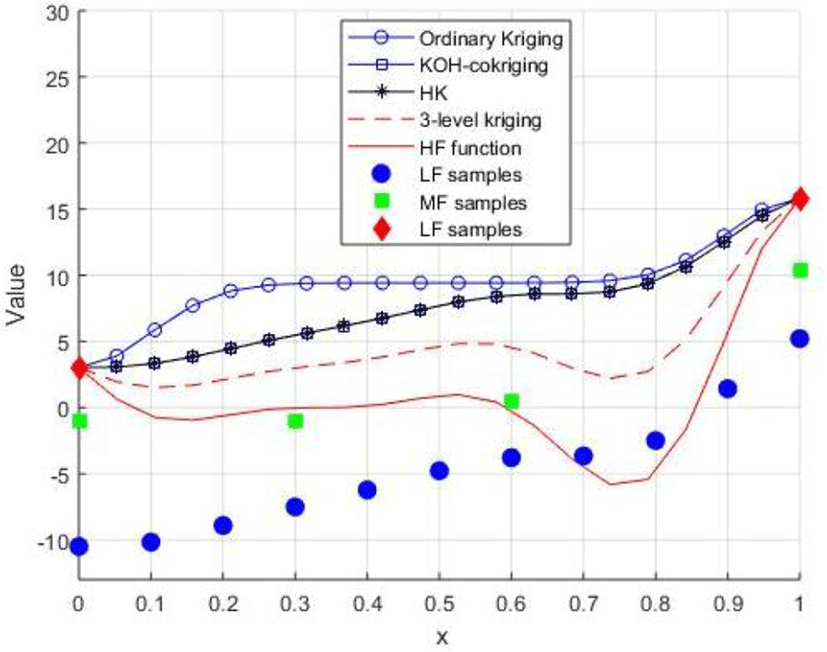
Numerical Experience with Variable-fidelity Metamodeling for Aerodynamic Data Fusion Problems
J. Def. Acquis. Technol. 2019;1(1):1-8.
https://doi.org/10.33530/jdaat.2019.1.1.1
HTML
PDF
PubReader
Last 3 months views: 519
https://doi.org/10.33530/jdaat.2019.1.1.1
An Assessment Model for Defense Cybersecurity Capability
J. Def. Acquis. Technol. 2020;2(2):39-43.
https://doi.org/10.33530/jdaat.2020.2.2.39
HTML
PDF
PubReader
Last 3 months views: 460
https://doi.org/10.33530/jdaat.2020.2.2.39
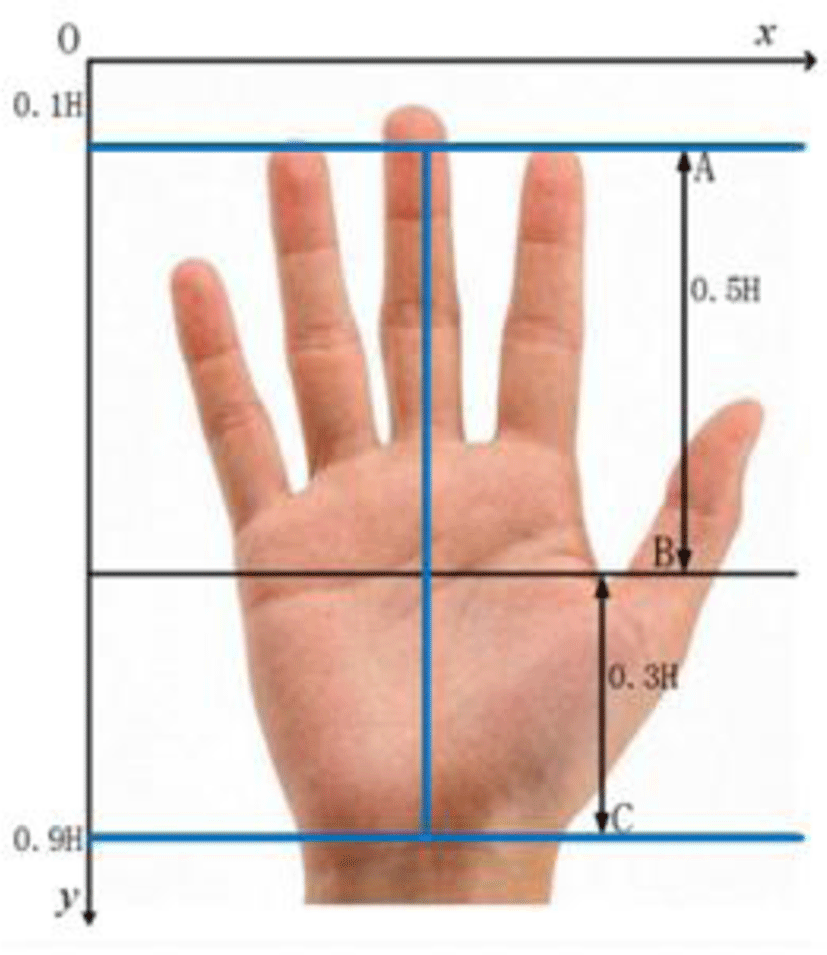
Key Point Localization Based on Intersecting Circle for Palmprint Preprocessing in Public Security
J. Def. Acquis. Technol. 2019;1(2):24-31.
https://doi.org/10.33530/jdaat.2019.1.2.24
HTML
PDF
PubReader
Last 3 months views: 322
https://doi.org/10.33530/jdaat.2019.1.2.24
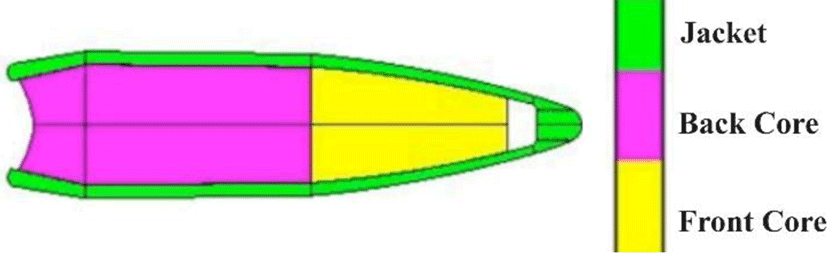
Experimental Consideration of Projectile Density and Hardness Effect on Its Penetration Ability in Alumina Target
J. Def. Acquis. Technol. 2019;1(1):9-15.
https://doi.org/10.33530/jdaat.2019.1.1.9
HTML
PDF
PubReader
Last 3 months views: 291
https://doi.org/10.33530/jdaat.2019.1.1.9
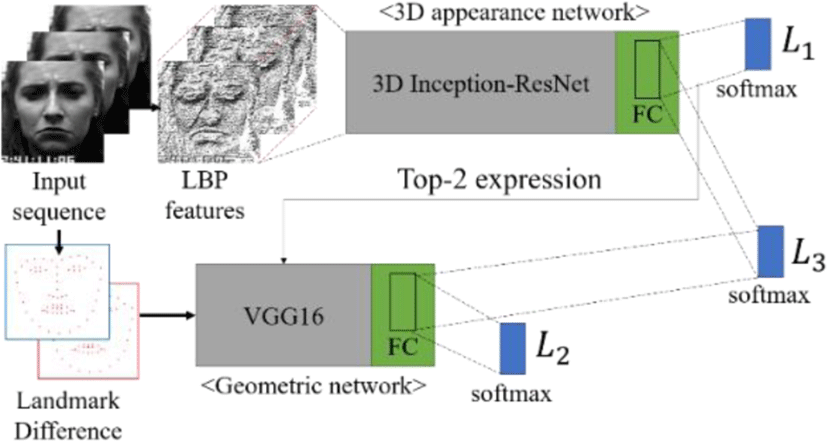
Real-time Facial Expression Recognition using 3D Appearance and Geometric Network for Public Security
J. Def. Acquis. Technol. 2020;2(1):33-37.
https://doi.org/10.33530/jdaat.2020.2.1.33
HTML
PDF
PubReader
Last 3 months views: 248
https://doi.org/10.33530/jdaat.2020.2.1.33








